Corporate OSINT for Social Engineering: Physical Security
There are many reasons why a threat actor may want to access an organization’s premises. They most usually boil down to installing surveillance devices, spyware (e.g., keyloggers), malware, stealing sensitive information or establishing a foothold to obtain remote control over internal systems. While imagination is the limit to what a bad actor can do, we know that the intentions are anything but good.
Physical social engineering attack simulations & vulnerability assessments help to proactively identify and implement realistic security measures. They evaluate an organization’s effectiveness in preventing unauthorized access to its premises. They effectively assess the level of difficulty an unauthorized individual would encounter to either covertly enter the organization’s premises or “talk their way in” by convincing authorized individuals to provide unauthorized access to a stranger under a pretext — a social engineering scheme.

Vulnerability assessments examine and/or test a number of potential vulnerabilities found within a system (physical, digital, human, or otherwise). Their goal is to inform the organization’s security strategy and provide actionable recommendations.
Physical penetration/intrusion tests tend to examine and/or test a number of potential vulnerabilities but then focus on a smaller number of them, build an attack simulation scenario around them, and put those vulnerabilities to the test. The end goal is to provide evidence of success or failure in a simulated attack scenario.
RECONNAISSANCE
Most social engineering attacks that involve a component of physical intrusion start with target reconnaissance. That means collecting information on the physical perimeter of their target organization and their people. A (simulated) threat actor will look for details about both the organization’s facilities and their surroundings (from geographical information to the civil infrastructure, the traffic and the roads around the facility, etc.), to security measures that are in place (badges, door types, and other systems) to insights about the building’s floorplans and entry procedures. The list is long, but the more you know about a facility and its “rules of the land” the better able you are to blend in or create an intrusion strategy that will work.
As security professionals, we can proactively follow the same process a threat actor would (through a physical penetration test or a vulnerability assessment) to identify information that exposes potential vulnerabilities in our organization’s physical perimeter.
There are two main ways to collect this information during the planning & preparation phase:
- Covert surveillance. It involves the physical presence of an individual in the proximity of a target organization’s premises.
- Open-source intelligence (OSINT) collection through digital sources. It can be conducted remotely and at any time.
I know a few penetration testers who simply decide to show up at a facility, try a standardized scenario, and see if it works. Sometimes, they perform some covert reconnaissance beforehand. Then they show up with an “I came- I saw- I conquered” mentality. It gets the job done. However, this approach’s success (and usefulness) depends heavily on the security maturity stage of the organization.
On top of it, as I tend to have a somewhat analytical personality, this approach does not satiate my work morale. I strongly need to dig deeper and conduct a more thorough review of the vulnerabilities that lay in plain sight — always depending on the client’s needs and requirements. At the end of each engagement, I consider it necessary to provide a holistic report of the vulnerabilities found — along with risk mitigation recommendations. Overall, I prefer to offer more insights than a simple: “Well, I came through the service personnel entrance, and you don’t really lock your doors, so I’m here now.” My professional conviction is that if we want a physical penetration test to be valuable and insightful, we need a more thorough approach than just trying to be lucky.
But let’s not divert.
As helpful as covert surveillance can be in identifying little nuances about your target organization (the flow of employees in and out of a building, the attention span or perceptual capabilities of a security guard, and other organizational details), it does not provide some essential information. Information that can instead be found online.
Open-Source Intelligence Resources & Techniques
In this blog, I focus on some of the OSINT techniques & resources that can be used in the vulnerability assessment of an organization’s physical perimeter.
In some cases, the research techniques are pretty straightforward but require viewing them with an adversarial mindset to be useful. Especially in the case of social engineering, it’s often not about employing the most extraordinary OSINT tool but about being able to analyze the information we find with the right mindset.
Exterior
I usually start by looking into the big picture of our target facility.
Online Mapping Services
Many of you are probably not shocked by this one. Utilizing Google Maps and Google Earth belong to the very first steps I take when I look into the physical perimeter of a site.
The process goes as follows:
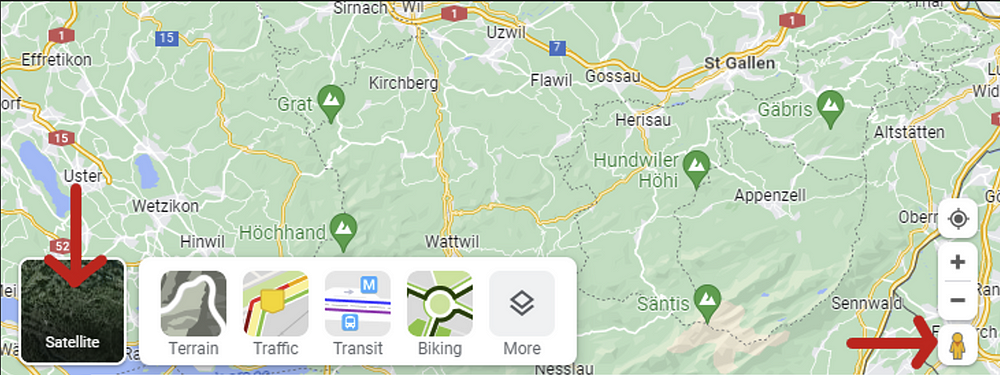
1. Enter Google Maps and type in the address of the target facility.
2. Apply the satellite layer view.
3. Conduct a first visual investigation (details below).
4. If available, enter the Street View mode (little yellow human icon on the bottom right of the map interface) to get a more detailed view of the environment.
A similar process is applied when using Google Earth. What’s different with Google Earth is that their street view is usually more detailed, they provide a 3D map viewing option, and they may have a more recent view of the site.
Note: always check for the year & month of the map data you are looking at! This information is usually found within a banner at the bottom of the map. If the images you are looking at are 1–2 years old, you should consider that there might have been significant changes in the meantime.
During this initial visual inspection, I usually look for:
· The location of the main entrance and its overall construction
· The pathway/surroundings leading to the main entrance
· Hidden entrances, especially at the back of the building along with the surroundings. Are there any doors that seem to be used by service personnel alone?
· External areas where employees seem to hang out
· The presence of a fence & the type of fence
· Potential security/guard posts
· Parking lots & how they connect to the main building
· Adjacent facilities (e.g., company cafeteria or restaurant)
· Surveillance equipment placement (sometimes these are very visible)
Field Notes
Why is this useful? In one case, the entire façade (front part) of a building we were working on had several security measures: Guard posts, two security doors leading to the main building, and cameras. But, upon closer inspection through mapping services, we also noticed a smaller, hidden entrance at the back of the building that was not protected by any fencing and, ultimately, was leading straight into the main building. Not only was that entrance easy to access, but it was also somewhat concealed, as it was right next to a small forest in the area. As we later learned during the briefing with the client, they somehow had ignored and forgotten that entrance, left it “probably unlocked most of the time” as some service personnel was regularly going in and out, and there was no camera in that area of the building and no lighting during the night. Quite literally, it was a very, very ignored (but useful) entrance. This would be an easy shortcut to the premises for a threat actor. If they decided to impersonate a service employee entering that door, it would probably not strike bypassers as something odd.
In another case, we found out that although the main building had enough security technology and processes around the main entrances, they also had an adjacent café/restaurant operating under a third-party partner and catering to the employees. Taking a closer look, we could see that the cafeteria was accessible from the street. Technically, a social engineer can easily hang around in such an open environment to eavesdrop on conversations and strike up a conversation with anyone sitting nearby, especially during busy lunch hours. Making acquaintances within that group by posing as a new hire and following them back into the building is a historically successful methodology.

Later on, by uncovering public data on their floorplans and an inside view through some public marketing videos, we also found out that the adjacent cafeteria had a connecting door to the main building with no security measures in place.
There are endless examples demonstrating how valuable mapping services have been. Still, the point is that you can gather an extensive array of information through simple, open-source services like the above to help you start discovering potential blind spots in the physical security of a target facility. Ideally, a security professional will find them before a threat actor does.
Are you one of the organizations that have removed/concealed your premises from popular mapping services?
The stakes are high. Your organization is probably conducting sensitive or high-value work, and you have plenty of reasons to take all the steps necessary to conceal your facility within the popular mapping services. Physical security is of the highest priority.
You are not out of the woods yet.
Mapillary and KartaView are two popular platforms that crowdsource street-view level imagery and map data and make them available to scale.
An important aspect: since all the images are crowdsourced, they cover areas that Google Maps and Street View would never get to. We check those websites at every project to identify unedited details of importance.
In certain instances, those images had captured personnel that was supposed to remain unidentified, entering an otherwise “concealed” site. There were cars with clear plate numbers that belonged to employees working within those facilities. You never know what a bypasser will happen to capture and upload, and therefore, it is a good idea to check this very public but less-known corner of the internet.
Interior Spaces
We can gather a wealth of information about the external perimeter of a site through both online and offline reconnaissance. But what about its inner areas and layout?
Plenty of information can be found with the right mindset and the appropriate search queries/ dorks. I will use Google Dorks as an example. However, the search engine you use will depend on the country your facility of interest is located in, along with some other parameters.
Floor Plans & Blueprints
Different professionals and companies must work together to bring a building to life. On the most fundamental level, an architect and a building company will be involved in building a facility and, in many cases, an interior designer, too. These contractors are businesses that also need to develop their own project portfolios and market their services. They do so by showcasing previous work through references or case studies on their websites. These portfolios often include detailed images from the interior of a building, blueprints, and floor plans.

A threat actor can use these details to map out how to move within a building, any potential hiding areas or emergency exits, and to build familiarity with the facility’s interior. As security professionals, we do not want to offer this convenience.
Check whether these resources are available through search queries such as:
“Company Name” AND “location” AND “architect”
“Company Name” AND (construction OR builders)
“Company Address” AND “interior design”
…and so on. Let your imagination run free with the combination of keywords.
Don’t forget to translate the keywords in the language of the country the facility is located in. In Europe, it rarely makes sense to perform these searches in English.

Sometimes, news articles discuss the architects/ interior designers behind specific “big” projects. In these cases, you tend to readily collect the names of the contractors involved in the project and conduct searches with more specific terms.
Video Footage
YouTube is a search engine, too, and a particularly helpful one when looking for recent footage of the inner spaces of a target company. It is not rare for both companies or recruitment agencies to upload interviews with current employees, office tours, and demonstrate the beautiful design work within the building and the amenities offered in order to attract talent. Those videos can also be found in the recruitment page of the company. Other times, they are found in partnering recruitment agency websites. You can find them in all cases by creating relevant search queries that will bring them to the surface. You may apply those search queries either directly on YouTube’s search bar, or in the search bar of your preferred search engine. Preferably both.
Keywords matter. Here are a few combinations you can try out:
“Company Name” AND:
· “working at”
· “a day in the life”
· “vlog”
· “interview with”
· “welcome to”
· “company culture”
· “meet the”… (usually refers to various work positions or people in the company)
· “office tour”
When I go through these videos, I usually focus on creating a more visual context for the blueprint/floor plan I might have gathered earlier. I also look for details that may be useful in an engagement.
For example:
· The types of doors & locks within the building
· The types of document storage cabinets & their locations
· Where the stairs & exits are located
· Whether the offices have glass walls or glass doors
· The front desk/ entry process
The last point is particularly handy. Many videos will, at some point, show the protagonist walking from the outside and entering the building. During those few seconds, you can often clearly follow the procedure required for entry. This can include badging your way in (and the type of badge), whether there is a front desk process, the hallway, the security measures in place, etc. If you are preparing a physical intrusion, this information will likely be included in the planning of an attack.
My 2 cents of advice: if your company decides to film an interview within the premises, advise them to blur the background and avoid walking through areas that provide insights to malicious actors. Alternatively, it is recommended to skip showing the entire entry procedure or to set up the recording in lower-risk areas of the building. Still, this is not always possible. Another option could be to install more invisible security measures around the entrances or where appropriate.
OSINT Is A Never Ending Story…
Initially, I wanted to include many more resources and OSINT research areas, but this blog is already too long and I don’t want it to get daunting. I hope that the above tips are providing a good start. You may also read my previous article for more resources on conducting OSINT for Social Engineering engagements.
If you are responsible for the physical security of your organization, a penetration tester, or a social engineer, you can make sure to check the above areas and include them in your report. The report alone can give plenty of good insights even if an attack simulation fails.
I hope you picked up some good tips and that you will use them to strengthen your organization’s security posture!
Do you need additional help or a more in-depth approach to conducting a physical security vulnerability assessment? Feel free to connect with me on LinkedIn or X/Twitter and let me know!

